American Food | American Dishes | American Desert | American Burger | American Restaurant | Search & Enjoy Your Favourite Food and Dishes
Following are the list of best awaresome videos on "Cyns6wzo') Or 313=(select 313 From Pg_sleep(15))" which you can watch online here or download.
 SQL Injection 101: Exploiting Vulnerabilities
SQL Injection 101: Exploiting Vulnerabilities
shorts. DOWNLOAD
 SQL injection | Web attacks | Web Technology | Lec - 58 | Bhanu Priya
SQL injection | Web attacks | Web Technology | Lec - 58 | Bhanu Priya
Web attacks & prevention SQL injection. DOWNLOAD
 PostgreSQL Security Features: Episode 6 - SQL Injection Attacks
PostgreSQL Security Features: Episode 6 - SQL Injection Attacks
An SQL #injection attack is an attempt to compromise a database by running SQL statements that provide clues to the attacker as ... DOWNLOAD
 SQL Injection Explained | SQL Injection Attack in Cyber Security | Cybersecurity | Simplilearn
SQL Injection Explained | SQL Injection Attack in Cyber Security | Cybersecurity | Simplilearn
Post Graduate Program In Cyber Security: ... DOWNLOAD
 Dangerous Codes: SQLi
Dangerous Codes: SQLi
short #infosec #sql #sqlinjection. DOWNLOAD
 SQL Injection 💉
SQL Injection 💉
SQL injection attack explained in hindi ▻Checkout my English channel here: ... DOWNLOAD
 SQL injection attack, querying the database type and version on MySQL and Microsoft
SQL injection attack, querying the database type and version on MySQL and Microsoft
filter?category=\'# GET /filter?category=\'UNION+SELECT+NULL,NULL# GET /filter?category=\'UNION+SELECT+\'aaaa\',\'bbbb\'# ... DOWNLOAD
 what is an SQL Injection?
what is an SQL Injection?
Join the NetworkChuck Academy!: https://ntck.co/NCAcademy ☕☕ COFFEE and MERCH: https://ntck.co/coffee #sqlserver ... DOWNLOAD
 What is SQL Injection? | SQL Injection Tutorial | Cybersecurity Training | Edureka
What is SQL Injection? | SQL Injection Tutorial | Cybersecurity Training | Edureka
Cyber Security Course (Use Code \"YOUTUBE20\"): https://www.edureka.co/cybersecurity-certification-training This Edureka ... DOWNLOAD
 SQL Injection For Beginners
SQL Injection For Beginners
Membership // Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into ... DOWNLOAD
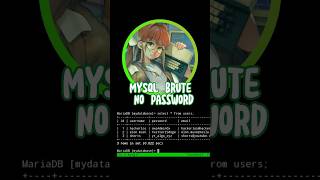 MySQL Brute No Password | NMAP & MySQL Injection #metasploit #mysql #nmap #ethicalhacking #termux
MySQL Brute No Password | NMAP & MySQL Injection #metasploit #mysql #nmap #ethicalhacking #termux
MySQL Brute No Password | NMAP & MySQL Injection #nmap #metasploit #ethicalhacking #mysql #sql #sqlinjection nmap, nmap ... DOWNLOAD
 UNION SQL Injection to Extract Data From Other Tables!
UNION SQL Injection to Extract Data From Other Tables!
Learn about SQL Injection vulnerabilities. In this video, we are going to have a look at a UNION SELECT query to extract data from ... DOWNLOAD
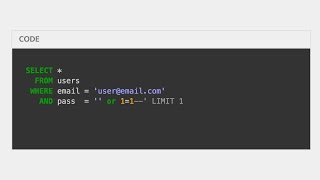 What Is SQL Injection?
What Is SQL Injection?
SQL injection is the most common and dangerous method used by hackers to attack websites. DOWNLOAD
 SQL Injections are scary!! (hacking tutorial for beginners)
SQL Injections are scary!! (hacking tutorial for beginners)
Is your password for sale on the Dark Web? Find out now with Dashlane: https://www.dashlane.com/networkchuck50 (Use code ... DOWNLOAD
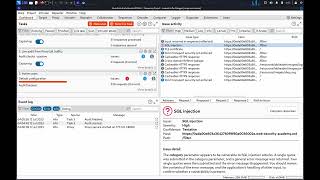 Testing for SQL injection vulnerabilities with Burp Suite
Testing for SQL injection vulnerabilities with Burp Suite
SQL injection vulnerabilities occur when an attacker can interfere with the queries that an application makes to its database. DOWNLOAD
 What is SQL Injection?
What is SQL Injection?
Learn more about SQL injection vulnerabilities and how to prevent a SQL injection attack. DOWNLOAD
 SQL Injection - Simply Explained
SQL Injection - Simply Explained
A simple way to explain the basics of SQL injection through interpretive animation. DOWNLOAD
 Hacking Websites with SQL Injection - Computerphile
Hacking Websites with SQL Injection - Computerphile
Websites can still be hacked using SQL injection - Tom explains how sites written in PHP (and other languages too) can be ... DOWNLOAD
 PostgreSQL Associate Tables and Conditional Insert - How To
PostgreSQL Associate Tables and Conditional Insert - How To
postgres #database #data We\'ll go over associating tables and conditionally inserting data in PostgreSQL. Buy the full course ... DOWNLOAD
 Running an SQL Injection Attack - Computerphile
Running an SQL Injection Attack - Computerphile
Just how bad is it if your site is vulnerable to an SQL Injection? Dr Mike Pound shows us how they work. Cookie Stealing: ... DOWNLOAD
 you need to learn SQL RIGHT NOW!! (SQL Tutorial for Beginners)
you need to learn SQL RIGHT NOW!! (SQL Tutorial for Beginners)
Keep your database of accounts and passwords secure by using DashLane! Sign up now at ... DOWNLOAD
 SQL injection attack practically explained - cyber security - part1
SQL injection attack practically explained - cyber security - part1
Hi, watch then like and subscribe. Its all about live practical sql injection understanding. DOWNLOAD
![[Hindi] SQL Injection Attack Explained | Practical Demo | SQLi [Hindi] SQL Injection Attack Explained | Practical Demo | SQLi](https://img.youtube.com/vi/lwqACxcFOO0/mqdefault.jpg) [Hindi] SQL Injection Attack Explained | Practical Demo | SQLi
[Hindi] SQL Injection Attack Explained | Practical Demo | SQLi
CyberAwareHub SQL Injection Attack Explained What is SQL injection attack? SQL injection attack explained in Hindi. What is ... DOWNLOAD
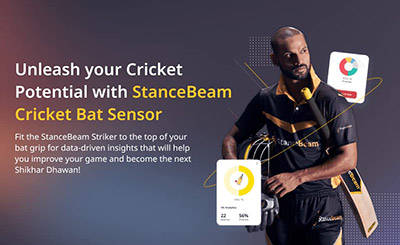
StanceBeam Striker | Cricket Bat Sensor to Improve Your Batting

IPL 2022 Special Gift | Whitedot Falcon Kashmir Willow Cricket Combo Kit Set

IPL 2022 Special Gift | NHD WRF Kashmir Willow Cricket Bat with Leather Ball

Lycan Dynamic Power Hard Plastic Cricket Bat for Tennis Ball and Wind Ball

Kore PVC 10-30 Kg Home Gym Set with One 3 Ft Curl and One Pair Dumbbell Rods with Gym Accessories

IPL 2022 Special Gift | Freebowler Non Electric Portable Cricket Ball Thrower | Bowling Machine | Pitching Machine

IPL 2022 Special Gift | boAt Airdopes 141 True Wireless Earbuds with 42H Playtime